The ideas Lockstep is presenting in our Data Verification Platform model didn’t spring up overnight. They can be traced back more than a decade to 2011 — and in some cases all the way back to last century.
In 1999, Stephen Wilson proposed that authentication technologies should be about more than just personal identity.
The idea that PKI certificates in particular could protect personal attributes against so-called identity theft was first written down in 2007 and presented to the Australian government’s Access Card inquiry.
This timeline sketches out the rest of the story. All items have been written by Stephen Wilson except where noted.
1999
Privacy positive aspects of public key infrastructures, Privacy Law & Policy Reporter 190.
“Authentication needs to encompass the ability to prove your business relationships, authorisations, membership(s), delegations, and so on, as well as — or instead of! — your personal identity.”
2004
Patent application: System and method for anonymously indexing electronic record systems for anonymous digital certificates asserting particular attributes — such as health system identifiers, biometrics, or other personal data — rather than identity.
Couched in legalese, this was a very early specification of what are now called verifiable credentials.This became US patent 8,347,101, granted in 2013.
2007
Conveying the pedigree of identifiers using digital certificates (PDF), Lockstep Babysteps No. 11. This was also presented to the Senate Finance and Public Affairs Committee’s inquiry into the Access Card legislation 2007.
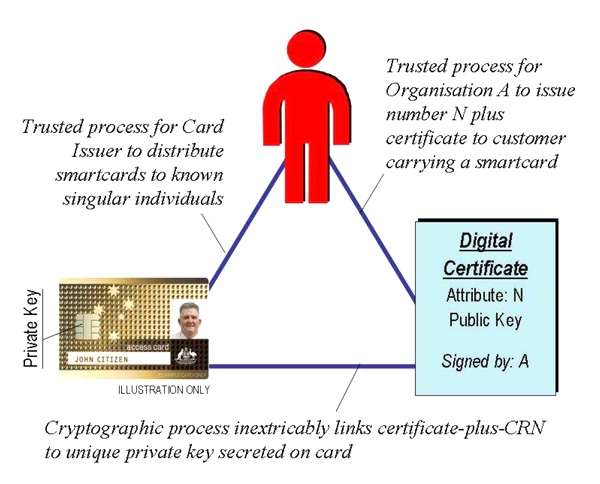
“The root cause of much identity theft and fraud today is the unfortunate fact that customer reference numbers and personal identifiers are so easy to copy. Simple numerical data like bank account numbers can be stolen from many different sources, and replayed in bogus transactions. In some cases, identifiers like credit card numbers can be simply made up, without merchants being readily able to tell the difference…
“There are ways of issuing personal data to a smartcard that prevent those data from being ‘claimed’ by anyone else, copied from one card to another, or simply made up. One way to do so is to encapsulate and notarise personal data in a unique digital certificate issued to a smartcard.”
2009
Written submission (PDF) and in-person testimony (PDF) to the Inquiry into cybercrime by the Australian Parliament’s House of Representatives Standing Committee on Communications.
We called for cryptographic technology to be deployed to make stolen data useless to criminals.
“To really curtail digital identity theft, steps must be taken to render stolen personal data useless to thieves, thus removing the profit motive for organised ID theft and neutralising the identity black market.”
“Smartcards [or smartphones] can be used by individuals as secure ‘containers’ to hold one or more personal identifiers, pseudonyms, log-on credentials and so on. When accessing a particular service, the card can work out precisely which identifying information is relevant in that context; the card will then release just the right amount of information to authenticate the user, and no more. Controlling the release of identity information is an important key to privacy, and limits exposure of personal data to identity thieves.”
2011
Forget what they taught you about authentication.
“The business you’re dealing with usually wants to know what you are, not who you are… The real challenge is to preserve the integrity, authenticity and pedigree of the different identities we already have when we exercise them online.”
Identity Evolves: Why Federated Identity is easier said than done, AusCERT 2011.
Grand identity federations such as the National Strategy for Trusted Identities in Cyberspace (NSTIC) and GOV.UK Verify, and promising products such as Windows CardSpace, have failed. If reusable identity is such a great idea, why is it so hard to achieve? It’s simple: Businesses don’t like to take other peoples’ word for who a customer is.
My ecological hypothesis about the true composite nature of digital identity provides crisp, new, plain-speaking explanations for why federation is so hard. Reusing identities across domains is like dropping a freshwater fish into the sea. All fish look superficially the same, just as the many identities in our wallets are all very similar, but each has evolved to suit a particular niche.
2013
US patent 8,347,101 was granted.
Identity is in the eye of the beholder.
“’Identity Providers’ do not in fact provide identity. They really can’t provide identity at all, but only attributes that are put together by Relying Parties in order to decide if a user or customer is legitimate. The act of identification is a core part of risk management. Identification means getting to know a Subject so as to make certain risks more manageable. And it’s always done by a Relying Party.”
Fractional Identity: An Alternative to NSTIC, George Peabody and Stephen Wilsion, re:ID magazine.
We exposed the fundamental blockage in federated identity, namely that the way you are known in one context is not exactly the same as in any other context. Subtle variations in risk and relationship management create untold complexities.
“[We] advocate for component claims, attributes, and data signals to be shared. If an organization knows something specific about me, my delivery address for example, as a result of them identifying me, then that organization can vouch for that signal to other relying parties. And get paid for it.”
Attribute wallets.
“What we’re talking about are specific factoids about the first party to a transaction (the Subject) that are interesting to the second party in the transaction (the Relying Party or Service Provider)…
“As much as we’re all interested in identity and trust online, the authentication currency of most transactions is attributes. The context of a transaction often determines (and determines completely) the set of attributes and their target values that together determine whether a party is authorised or not.”
“My vision is of digital wallets. I advocate that users be equipped to hold close any number of recognised attributes in machine readable formats, so they can present selected attributes as the need arises, directly to Relying Parties.”
2014
Safeguarding the pedigree of personal attributes.
“To restore the reliability of personal attribute data, we need to know their pedigree. We need to know that a presented data item is genuine, that it originated from a trusted authority, it’s been stored safely by its owner, and it’s been presented with the owner’s consent.”
2018
A Digital Identity Stack to Improve Privacy in the Internet of Things (PDF), Stephen Wilson, Nour Moustafa, and Elena Sitnikova, IEEE World Forum on IoT, Singapore.
Articulates the use of verifiable credentials for cars to convey warranty, manufacturer, service history, standards certification, and other information.’
US patent 10,164,966: Decoupling identity from devices in the internet of things.
This invention extends verifiable credentials to non-human subjects.
2019
Data Protection Infrastructure for the Digital Economy (PDF), based on a presentation to Technology in Government, Canberra.
The first suggestion of Click-to-Prove. “Citizens should be able to move trusted copies of their personal data around the digital economy as easily and as safely as they move their money.”
2020
A capability maturity mode for personal data carriers and digital wallets
This essay charts the evolution of credentials from plastic through chip to smart devices.
2021
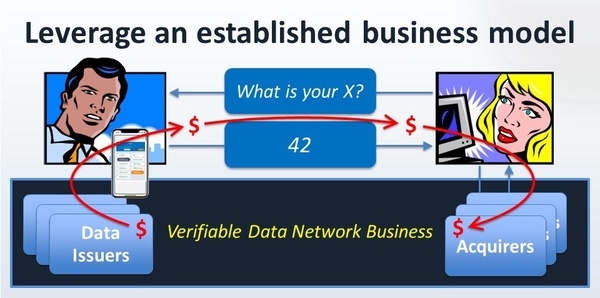
Why Isn’t Identity Easy? (written summary) outlined a “Verifiable Data Network Business” with a four-party structure, before the GAIN whitepaper (PDF) came out independently describing something similar. We have since developed a comprehensive and distinct role for the fourth party, describing it as the data distributor. This speech also introduced the concept of “Tap to Prove”.
2022
If data is the new black (gold) how do we protect the supply?
Argues that just like the oil industry, the data industry will need a new infostructure of laws, regulations, and systems for ensuring quality and to protect the environment.
FIDO leads the way for a verifiable IoT
The FIDO Alliance has helped to embed a standard cryptographic stack that extends from the cloud all the way out the edge, where computerised devices increasingly come with a built-in basket of security and privacy primitives for developers to leverage.This post is based on a speech to the FIDO Authenticate Conference, 2022.
Video: What will we learn from the market failure of digital identity?, a presentation at Identiverse 2022.
Argues that the standard model of digital identity has failed, and that “our digital tools and practices re-purposed for a bigger and grander problem”.
Video: Trust in a post identity world #ZeroIdentity, the closing keynote at Identiverse 2022.
Argues that we need to move the conversation beyond identity and imagine a world where cryptographic infostructure makes data as trustworthy as electricity or clean water.
Handout: Trust in the post-identity world, summarising that closing keynote.
How to Create an Infostructure to Protect Data as a Utility, Australian Quarterly special election edition.
This feature in one of Australia’s leading public policy journals examines “how to systematically safeguard the distribution of this critical resource”, namely data.
“Waving a phone is fast becoming a uniform user experience, as familiar as inserting a plastic card into an ATM. Behind the scenes there are rigorous business processes, checks and balances whereby credential issuers are given trusted access to the wallet hardware and operating systems. It is difficult for banks and healthcare authorities to have their credentials approved by Apple, and so it should be…
“Government is the foundation for most of the atomic truths of interest day-to-day. The best thing governments can do now is refocus on the concrete and make all the facts and figures for which they are authoritative available to citizens in verifiable digital form. Only then will true digital citizenship follow, when we can move verifiably true copies of important data around as simply and safely as we move our digital money.”
A new chapter
George Peabody, renowned global payments expert, joined Lockstep as a partner to continue a unique collaboration to define data sharing infostructure. This is now Lockstep’s focus, complementing our continuing core business in analysis and advice in data protections, information privacy, and digital identity.
2023
Handout: How a data protection infostructure can safeguard value chains, based on a presentation at CyberCon, Canberra.
An overview of how verifiable credentials can be deployed to quickly lead to a data verification infostructure.
Digital wallets are components, not systems, George Peabody.
“Wallets are a useful component, but they are only worthwhile when there is an arrangement between parties to govern which credentials are fit for purpose in each transaction they wish to conduct.”
Putting government data to full use — and why, George Peabody.
Proposes a shift in how government provisions verified credentials into the wider economy. The result will be a more resilient data ecosystem across multiple use cases.
DVP in a Nutshell (PDF)
The rationale behind the Data Verification Platform model in a single page.

Stephen Wilson will be speaking at Identiverse 2023 in late May. Stay tuned…
Follow the evolution
If you’d like to follow the development of the Data Verification Platform model, please subscribe for email updates.
