Lockstep Technologies MDAV Stage 1 Certificate Policy (1.0.1), v1.0, July 2016.
Acknowledgement
The Mobile Device and Attributes Validation project is funded by a Department of Homeland Security Science & Technology grant. The work is conducted by Lockstep Technologies under the auspices of the Kantara Identity and Privacy Incubator (KIPI) and the Command, Control and Interoperability Center for Advanced Data Analysis (CCICADA) at Rutgers University.
Extract
The full policy document available here.
1. Introduction
This is a master Certificate Policy for the Mobile Device and Attribute Validation (MDAV) PKI, setting out baseline policy requirements for all MDAV certificate issuers, and indicating where detailed policy variations are to be made for different communities of interest and Attribute Authorities.
1.1 Overview
The MDAV system deploys anonymous and pseudonymous X.509 certificates to users of approved mobile devices. Certificates are issued from a hierarchy of Certification Authorities and virtual CAs representing Attribute Authorities. All CAs chain to a Root CA dedicated to the MDAV community.
1.2 Document name and identification
Certificates issued under this CP shall bear the Policy OID:
1.2.36.109313411.1.10.1.X
where:
- 2.36.109313411.1.10 is the MDAV Root CA at top of the MDAV PKI hierarchy. The RCA has its own CP.
- 2.36.109313411.1.10.1 is this master Certificate Policy.
Further leaves will be uniquely allocated to different organisations acting as Attribute Authorities recognised within the MDAV community.
MDAV Certificate Policies and Certificate Practice Statement will be published at https://lockstep.com.au/technologies.
1.3 MDAV PKI Participants
In overview, MDAV certificates carry copies of particular attributes issued to individuals by Attribute Authorities (such as credentialing bodies for First Responders). A registration process provisions an MDAV certificate to a particular Subject and a key store on a mobile device controlled by the Subject. Only MDAV-approved mobile devices may carry MDAV certificates; this rule is enforced by the registration process.
Participating Attribute Authorities use a Certificate Management System (CMS) to interface the registration process to a CA in the MDAV hierarchy. Certificates are issued by each AA’s CA under a Certificate Policy specific to that AA, and carry a unique Policy OID. Each MDAV Certificate Policy will in particular specify the meaning of the attribute, the rules for a Subject to qualify for the attribute, any terms and conditions governing how the Subject should act in the context of the attribute, the normal lifetime of the attribute, conditions for renewing or cancelling the attribute, and details of the approved device(s) that the certificate may be issued to.
Each certificate issued within MDAV uniquely specifies (through the Policy OID):
- an attribute value assigned to the certificate Subject
- the identity of the Attribute Authority, and
- the type of device to which the certificate has been issued.
This set of facts may be securely conferred to any Relying Party by a certificate holder by digitally signing a message with the private key associated with the certificate.
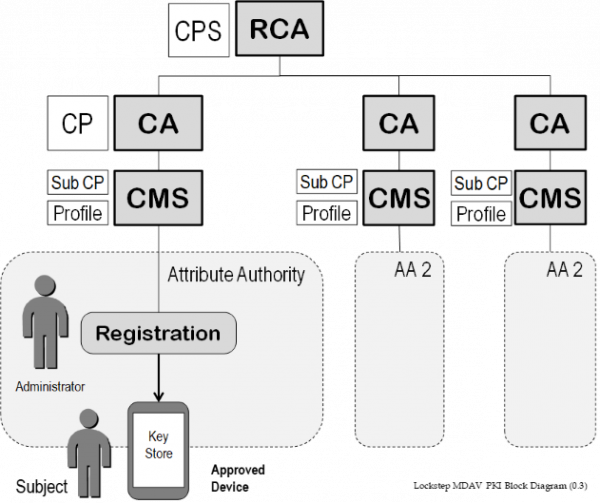
1.3.1 Certification Authorities
All CAs in the MDAV PKI are virtual CAs run by the MDAV Operator on behalf of participating Attribute Authorities. Each CA Certificate Policy is assigned a unique Policy OID.
1.3.2 Registration Authorities
All registration of MDAV certificate Subjects is done via a CMS accessed by authorized administrators of participating Attribute Authorities. Such administrators and their registration systems may be regarded as “RAs”. There are no separate RAs in MDAV.
1.3.3 Subscribers
All Subscribers (Subjects) of MDAV certificates are bona fide members of communities of interest represented by respective Attribute Authorities. Each Subject is known by an AA according to rules of that AA sufficient for an attribute value to be assigned to that Subject. The MDAV scheme plays no part in setting the membership or registration rules of Attribute Authorities.
Subjects may be issued multiple MDAV certificates by multiple AAs, to one or more approved devices.
1.3.4 Relying Parties
Relying Parties in the MDAV scheme are any individual or organisation choosing to interact with a Subject on the basis of the attribute and associated Attribute Authority. Relying Parties generally recognise the authority of an AA in a certain context.
Relying Party applications are to be written in order to transact with certificate Subjects in that context. Relying Party applications will need to each have a reliable copy of the MDAV Root Public Key and will need to recognise particular Policy OID values in order to validate a given Subject and their presented certificate.
1.3.5 Other Participants
Developers writing software that processes MDAV certificates will generally need to obtain information about Policy OIDs from the MDAV Operator.
1.4 Certificate Usage
1.4.1 Appropriate Certificates Uses
Each MDAV certificate is expected to be used to convey the fact that the Subject has been issued a given attribute value by the Attribute Authority named in the certificate (issuer field). Technically, MDAV certificates will typically be used to sign messages or digital objects originating from the Subject which are authorized in some context by way of the attribute value.
An MDAV certificate means nothing more and nothing less than the fact that the certificate Subject has been issued with a particular attribute value by the Attribute Authority named in the certificate.
Appropriate certificate uses will be precisely specified in a sub-policy specific to the Attribute Authority.
