Synopsis
The professional practices of information security and privacy are the opposite sides of the same coin. If identity management is what you need to know about someone in order to deal with them, then privacy is what you don’t need to know.
We should not sugar-coat privacy, for it does create tensions. The reality is privacy can be at odds with security, usability, cost, and revenue opportunity. And just as there is no such thing as perfect security, we cannot have perfect privacy either. This sort of real-world mindset helps security professionals make better sense of privacy regulations.
Engineering is all about trading off competing requirements, and so “privacy engineering” should bring privacy tensions to the surface and resolve them systematically. Some people are frustrated by the lack of closure in legal treatments of privacy, wishing there was more certainty. Yet security professionals deal well with uncertainty, so despite the ambiguities in the law, privacy principles can be dealt with in much the same way as information security, with professional estimations and judgements about risk.
This Masterclass will bring everything you need to know about privacy into plain view. It will equip security practitioners and other IT professionals to work effectively with the privacy function and will help you to avoid a range of common privacy snags.
Key points and a detailed agenda follow below, with some snapshots of the slides. Please contact Steve Wilson if you’d like the Master Class delivered for your organisation: swilson@lockstep.com.au.
Handouts (PDF)
Key Points
- The new definition of Personal Information (Privacy Amendment Act 2014)
- Surprises: Anonymity, category errors, Indirect Collection, data analytics
- How do we go from subjective “creepy” tests to objective privacy requirements?
- How can IP addresses be “personal information”?
- Gauging Privacy Risks in the Infosec TRA
- De-identification, and re-identification as a risk
- Treating privacy as a Data Asset
- What Big Data means for privacy
- How might we objectively re-balance national security and privacy?
Agenda
1. Recap: The functions, features and forms of Data Privacy Regulations
- Mapping Privacy Principles onto security practice
- A 360 degree view of Privacy
2. Bridging Infosec and Privacy
- Common Ground: Collection Limitation, Least Privilege and The Need to Know
- “Privacy by Design”
- “Privacy Engineering”
3. Case studies
- Apple Watch and fitness trackers
- Siri and Apple’s new privacy promise
- Google StreetView Wi-Fi collection
- Big Data : Target’s pregnancy detector
- Big Data: The controversial new European “Right to be Forgotten”
- Big Data: “DNA hacking”
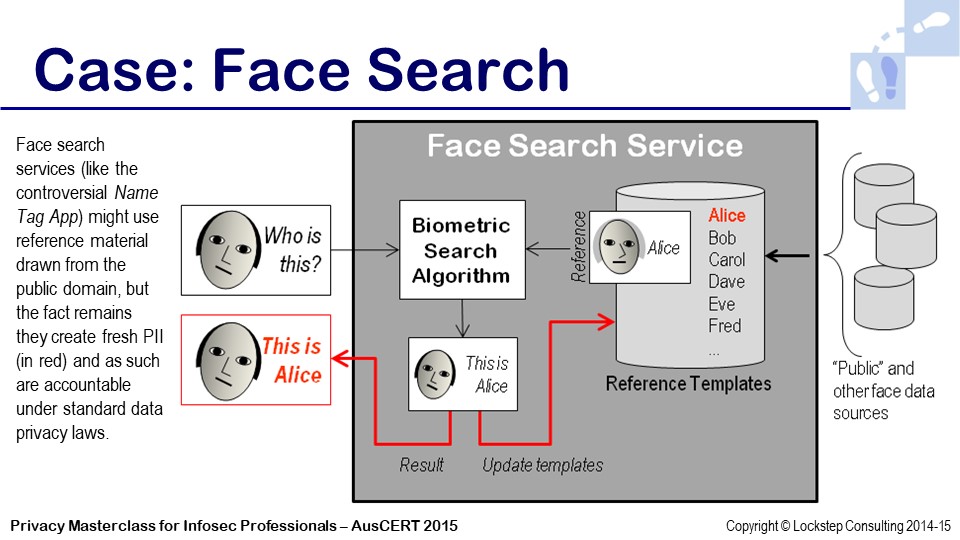
- Biometrics: Face search
- Biometrics: Why is Snapchat worth more than three billion dollars?
4. Practical Privacy Engineering
- Privacy in the Information Asset Inventory
- Privacy in the Threat & Risk Assessment
- Information Flow Mapping
5. Summary and Discussion