Abstract
Over time, payment cards, driver licences, and now Germany’s national eID have all climbed up a technological ladder to provide a mobile user experience. These are exemplars of a large set of almost mundane identification items, including student cards, membership cards, employee IDs, tickets, professional licences, and passports. Most of these items were first rolled out as pieces of paper or cardboard, and later took the form of more robust plastic cards. Where fraud is a problem, identification cards adopt a range of security features, both physical and increasingly digital. Smartcards with embedded reprogrammable microprocessors can prove the originality of a cardholder’s details and transactions, and smart phones add further layers of automation and extended anti-fraud features.
Fundamentally, all these identification tokens act as personal data carriers to help people prove their credentials in different contexts. This paper maps data carriers’ progression in automation, security and privacy protection onto the five-level Capability Maturity Model (CMM). Modern data carriers capable of holding and presenting multiple credentials are now popularly called digital wallets.
News: German national ID goes mobile
German citizens will soon be able to carry their national electronic ID (eID) on certain smart phones thanks to work being done by the German government’s Office for Information Security, Deutsche Telekom, and Samsung [1]. The solution involves cloning the eID smartcard ― which is NFC-enabled ― onto the phone’s secure element.
This development is simply the latest in a steady progression of digitisation of the German national identity system.
The same evolutionary path is evident across many different types of credential, classically starting with paper cards and progressing in stages through passive data carriers and “smart” cards to arrive at smart phones acting as wallets for multiple credentials. This lineage has played out in near-identical fashion (albeit at different rates) with credit cards and driver licences.
The capabilities of data carriers
This evolution of data carrier technologies can be mapped onto the familiar five level CMM. By vividly demonstrating how the pattern is repeatable might help to accelerate the modernisation of other credentials so the benefits of usability and fraud resistance get to be enjoyed more widely.
The evolution of this technology class has been described elsewhere [2]. To recap briefly, steady improvements ― firstly in data storage and then around cryptography ― have seen active or “smart” devices emerge with the ability to present verified data about their individual holders.
In retail payments, smartcards now dominate. What makes a smartcard “smart” is its ability to prove cryptographically that the cardholder was in control of a transaction. The user’s knowledge of a PIN or their possession of a biometric can be verified (matched) on the card itself. Not only that but each separate transaction is digitally signed by a private key within the chip unique to the cardholder, thus cryptographically marking the transaction as original. And furthermore, the cardholder data carried by the chip can be digitally signed (that is, certified) by the card issuer, in effect branding the account details and showing their provenance.
The cryptographically bound bundle of transaction and cardholder details produced each time a chip card is used carries forward the imprimatur of the issuer and cannot feasibly be counterfeited. The sophistication provided by smartcards has been replicated in the Secure Elements of smart phones and the Trusted Platform Modules of many personal computers.
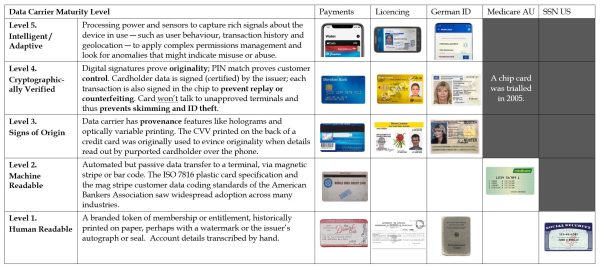
Five levels of maturity
The increasing power and sophistication of data carriers from paper cards through smartcards to smart phones and digital wallets can be characterised as follows.
- Human Readable. Plain text account holder details carried in a convenient form for human consumption; historically printed on paper, perhaps with a watermark, the issuer’s autograph and/or an official seal; data is transcribed by the receiver by hand.
- Machine Readable. Data carried in some sort of memory ― magnetic stripe, bar code or PROM ― so it can be automatically transferred to a terminal; data transfer is passive, reading from the card and writing to the terminal. The ISO 7816 plastic card specification and the magnetic stripe customer data coding standards of the American Bankers Association have dominated at this level and are widely used across many industries.
- Signs of Origin. The data carrier has provenance features such as holograms and optically variable printing, to frustrate illicit copying or counterfeiting. A prototypical digital provenance feature was the Card Verification Value (CVV) printed on the back of a credit card, which was originally used to evince originality when account details are read out by the cardholder over the phone; the CVV was not left behind on the carbon copies resulting from normal manual card processing and was therefore less accessible to the early “dumpster diving” ID thieves.
- Cryptographically Verified. A range of digital techniques dramatically strengthen the originality of the device and its actions. When a PIN or biometric must be matched to activate a card or some such, it proves that the customer was in control at the time a transaction was undertaken with the device. Digital signatures also prove originality in two respects. Firstly, cardholder data is signed (i.e. certified) by the device issuer when loaded into the device, and secondly, each new transaction is also signed in the chip to prevent transaction replay or counterfeiting. Further, a smartcard can be aware of the setting in which it is being used and respond to attempted misuse; for example, it should not talk to unapproved terminals, which prevents card skimming and cloning.
- Intelligent / Adaptive. Smart phones have the processing power and diverse sensors to capture a rich array of signals about the device in use, such as the user’s behaviour, their recent transaction history, time of day and geolocation. The device software can apply complex permissions management to control what the user can do and can look for anomalies indicative of misuse or abuse.
The Capability Maturity Model is illustrated in the following table using examples from selected industries. A more detailed discussion follows.
The model
Discussion
Payment cards
The credit card industry over a period of sixty years has been the prime mover of data carrier evolution, from Maturity Levels 1 through 5.
The American Banking Association standardised exactly how cardholder data is encoded in different tracks of the magnetic stripe. The same standard was widely adopted across many other industries for employee IDs, student cards, driver licences, mass transit tickets, healthcare, club membership cards, library cards, loyalty and government ID. Mag stripe coding, plus the ISO 7816 card specifications, created a universal plastic card UX, and Data Carrier Maturity Levels 2 & 3 became globally ubiquitous.
It seems digitisation in retail payments has been the main motivation for smartphone wallets like Apple Pay and Samsung Pay and thus the attainment of Data Carrier Maturity Level 5.
Driver licensing
Driver licences have advanced from fragile pieces of paper to plastic cards in most parts of the world. As licences morphed into broadly accepted de facto identity documents, they became prime targets for counterfeiting by organised crime, and so anti-fraud features have become commonplace, including holograms, optically variable printing and guilloche engraving.
In Australia, the state of Queensland introduced a chip in their driver licence over ten years ago, reaching Maturity Level 3 for perhaps the first time in the world. Many licensing authorities are now moving to mobile phone-based driver licences, often with bespoke QR code data carriage. The International Organisation for Standardisation is drafting a Mobile Driver Licence (mDL) ISO standard with NFC technology for secure data presentation.
Government entitlements in Australia and the USA
Australia’s universal public health insurance scheme Medicare has used a plastic card with magnetic stripe for decades. Over 2004-06 a small smartcard pilot was undertaken in the state of Tasmania. At first the objectives were simply to upgrade the mag stripe to make the card more difficult to clone or counterfeit. That initiative was then subsumed into a larger Access Card proposal with a broader mission to rationalise a number of social security accounts and reorganise them within a new national Human Services administration.
The chip-based Access Card attracted widespread protests for its semblance to a national identity, something most Australians have long resented. In 2007 a change of federal government saw the smartcard abandoned (at around the same time as the British government cancelled its national ID card project over broadly similar civil concerns).
No administration in Australia has ever returned to the worthwhile idea of simply upgrading the Medicare card to chip for fraud resistance, and the card remains at Data Carrier Maturity Level 2. Multiple proposals to adopt “Common Access Card” technology (the defence force smartcard) in the U.S. Medicare system have come and gone over the years.
The U.S. Social Security card notoriously has yet to advance past Data Carrier Maturity Level 1.
Conclusion: Smart data carriers and data quality
Chip cards (at Maturity Level 4, especially with NFC contactless connectivity) and the secure elements of smart phones (at Level 5) are increasingly important, with data carriers being used more and more in the digital domain. These technologies fundamentally protect the quality of the data they carry and present on behalf of their holders, as follows:
- Provenance: user’s details are certified by the issuing authority through a digital certificate bound to the chip
- Consent: each fresh transaction is digitally signed ― automatically and seamlessly ― on behalf of the user with a private key in the chip
- Possession: the fact that the device was unlocked by a PIN or biometric proves (to a reasonable degree of confidence) that the rightful user was in control of the transaction
- Privacy: the superior accuracy and provenance of user data presented from a cryptographic chip makes transactions reliable without further identification and exposure of personal data
- Originality: provenance and proof of possession allow a relying party to tell the difference between original Personal Data and counterfeited or stolen data.
With Data Carrier Maturity Level 5 now established in banking and driver licensing, this benchmark can be taken up in all sectors where mission-critical identifiers are an integral part of the system. Healthcare and social security are overdue for better ID protection. While privacy anxieties have dominated in these fields, the Data Carrier Maturity Model shows how IDs and personal details can remain separate and secure when upgrading to superior technologies. And the uniform user experience of mobile credentials ― cryptographically verified by sophisticated algorithms now standard under the covers ― can be naturally extended to all walks of life.
References
[1] Germany to begin rollout of open national digital identity service ‘later this year’, Sarah Clark, NFC World, 29 July 2020 [2] Reframing Digital Identity as Data Protection, Steve Wilson, Constellation Research, 25 November 2019.Acknowledgement
This article is adapted from my Constellation Research blog, A Capability Maturity Model for Data Carriers, 5 August 2020. It was originally published on LinkedIn.
Photo: Several smartcards by Diego.souto, Wikimedia Commons, used under the under the Creative Commons Attribution-Share Alike 3.0 Unported license.