Wilson, Stephen. “New models for the management of public key infrastructure and root certification authorities.” Information management & computer security 7, no. 4 (1999): 166-170.
Introduction
Around the world, possible key infrastructure (PKI) rollout has repeatedly stalled over the question of the peak authority or root certificate authority (CA). National governments have for the most part been reluctant to take responsibility for the peak authority. Their reasons have included fear of the liability thought to go with the top of the “chain of trust”, and philosophical doubts that it is proper or effective to try to “legislate” trust. Underlying these difficulties is a general lack of clarity about the objectives of PKI and its ability to deliver “trust”.
One key obstacle in the debate over the peak authority is that we have not clearly articulated the functions and benefits of the higher level CAs in the infrastructure; i.e. those CAs that a root CA signs. To be truly useful to relying parties, higher level CAs must do more than merely authenticate other CAs; they should additionally assert the proper operation of those CAs.
Another problem is that certificates are still predominantly thought of as simple electronic passports, identifying the holder to some arbitrary level of confidence. Yet much business is conducted between parties based on their presumed authority or credentials rather than their personal identity. A preoccupation with personal identification within PKI has generally overlooked the routine needs of business transactions and has obfuscated the proper role of the higher levels of the infrastructure.
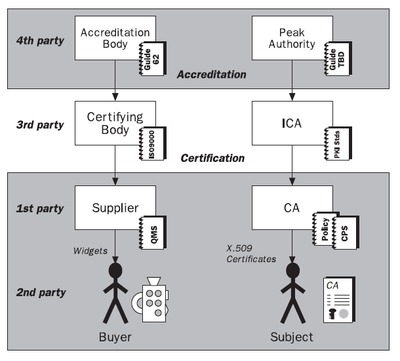
Postscript
In the years that followed, I found that schemes like Common Criteria are a much better model than ISO 9000. Yet the principles are exactly the same as I set out in 1999. Instead of ISO/IEC Guide 62, we could use the newer laboratory inspection standard ISO/IEC 17020. My 2008 paper “Public Key Superstructure” is clearer on this point, but lacks the detail of the 1999 paper.
